Sometimes law enforcement officials achieve so-called “consent” by being vague […] You can try to dispel this ambiguity by inquiring whether border agents are asking you or ordering you […] If an agent says it is a request only, you might politely but firmly decline to comply with the request.
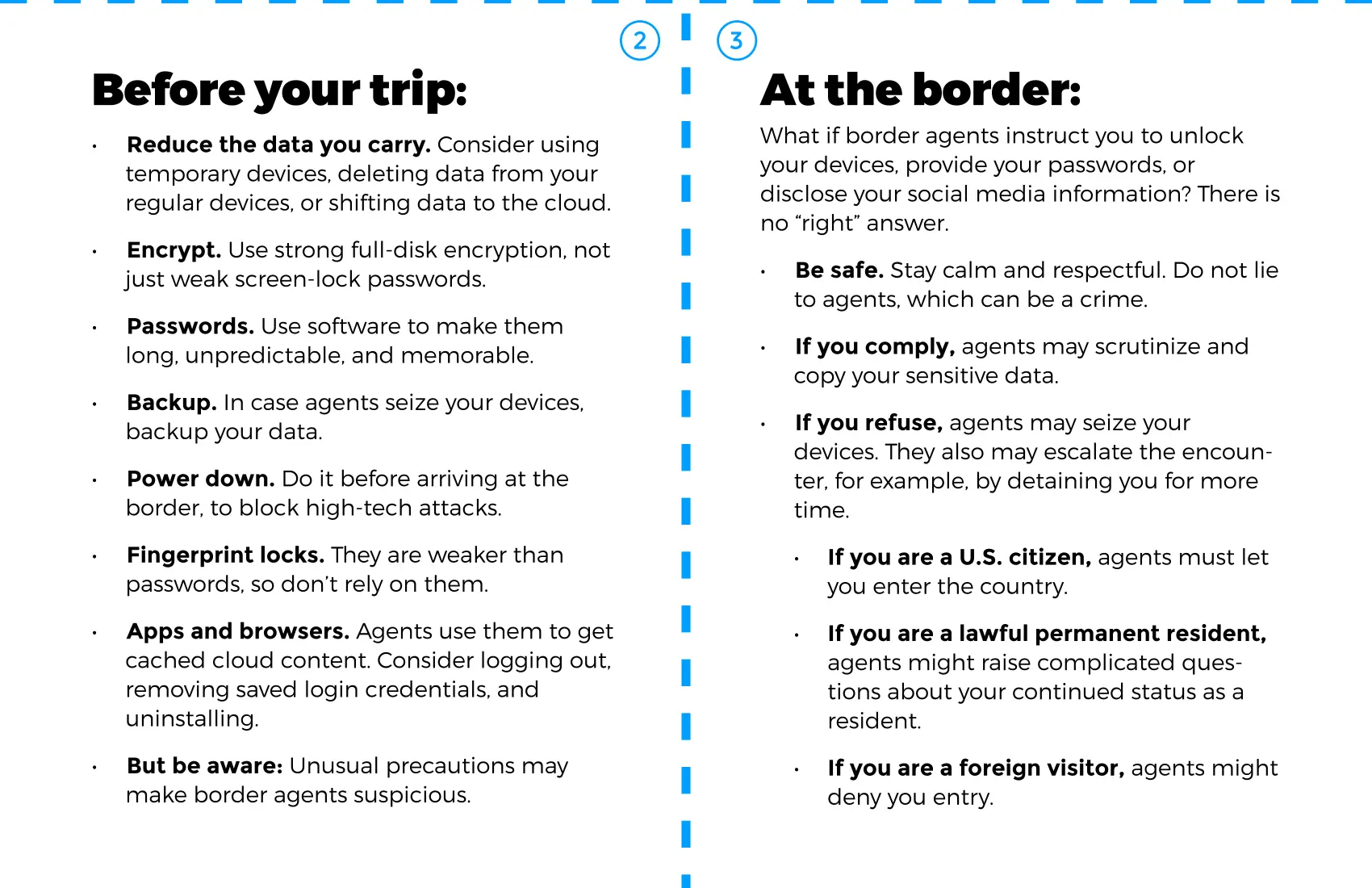
If you are a U.S. citizen, border agents cannot stop you from entering the country, even if you refuse to unlock your device, provide your device password, or disclose your social media information. However, agents may escalate the encounter if you refuse.
If you elect to comply with a border agent’s order to unlock your device, provide your password, or disclose your social media information, you can inform the agent that you are complying under protest and that you do not consent.
It is possible that if you unlock your device, and agents then search your device, a court will rule that you consented to the search. […] As noted in Part 1, the best way to avoid an inadvertent “consent” to search is to decline to unlock your device, provide the device password, or provide any social media information.
Technically, you don’t even need to admit that you know the password.
If you believe that border agents violated your digital rights at the border, please contact EFF at borders@eff.org.
Generally, votes are overrated. Especially if you’re not mainstream, by definition most people won’t support you, won’t agree with you, won’t understand you.
Some things may be downvoted because they’re too stupid. But occasionally, you might be downvoted simply because you’re a bit too early. Like, if you’d said “being gay is not crime” or something 50 years ago, you might have got downvoted… Just a thought.