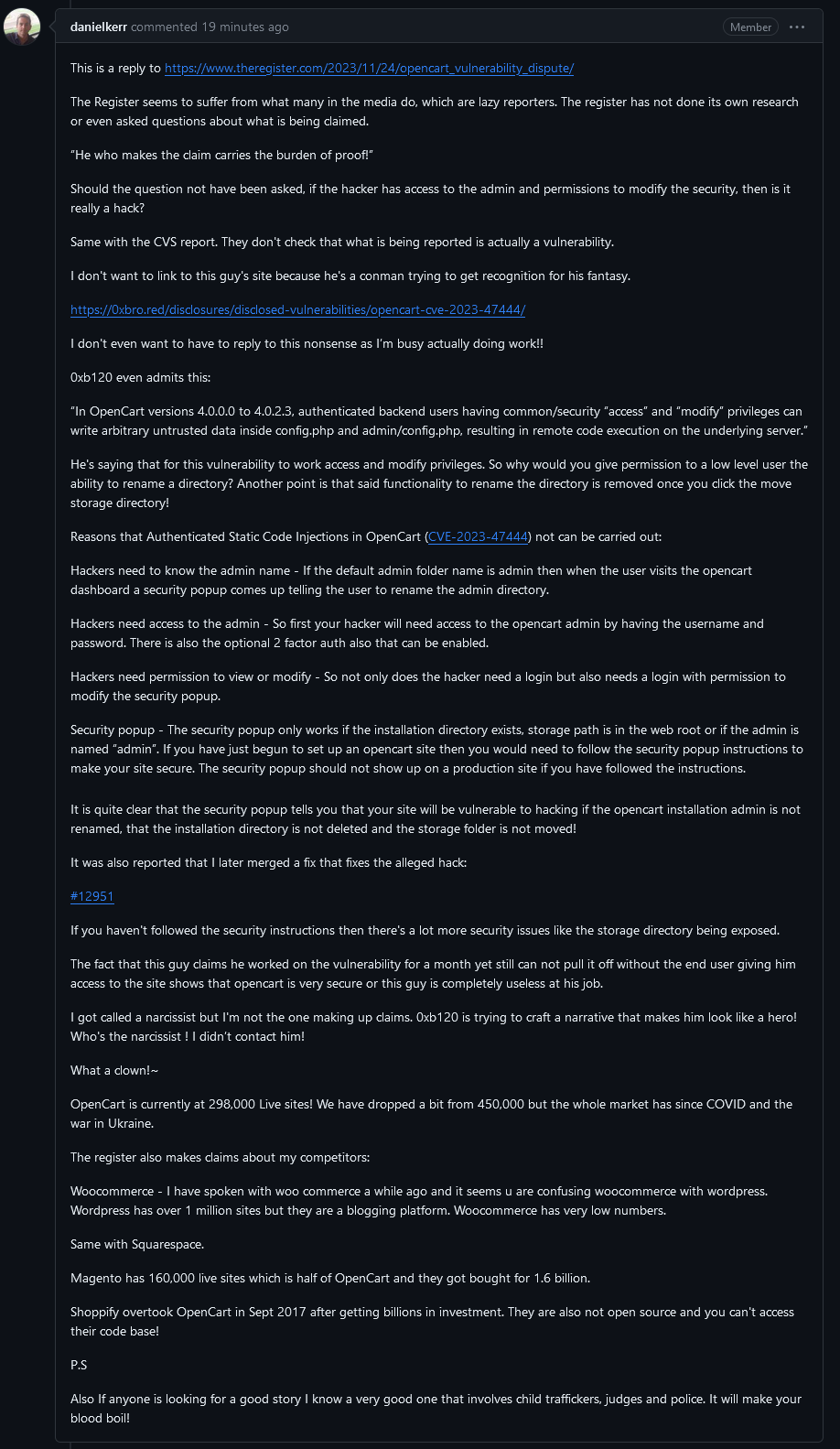
For context, this guy has a history of being dismissive of legitimate security concerns like using unsalted md5 passwords
Technology
This is the official technology community of Lemmy.ml for all news related to creation and use of technology, and to facilitate civil, meaningful discussion around it.
Ask in DM before posting product reviews or ads. All such posts otherwise are subject to removal.
Rules:
1: All Lemmy rules apply
2: Do not post low effort posts
3: NEVER post naziped*gore stuff
4: Always post article URLs or their archived version URLs as sources, NOT screenshots. Help the blind users.
5: personal rants of Big Tech CEOs like Elon Musk are unwelcome (does not include posts about their companies affecting wide range of people)
6: no advertisement posts unless verified as legitimate and non-exploitative/non-consumerist
7: crypto related posts, unless essential, are disallowed
Yikes, that is embarassing.
Is opencart written in PHP? Bcrypt has been a thing for decades now, and is literally a drop in replacement that handles salting et al. If the developer was hesitant to implement that, I'd rather go use Magento or shudder Shopify
One of the first things I did when I took over an old php project was convert to bcrypt and add logic to automatically upgrade the hash on their next login (and in case you're wondering, we also removed the old insurance hashes and the upgrade logic after a while, forcing remaining users to do a password reset).
This is one of the things I talk about when people ask what the difference is between junior and senior developers.
A lot of security is just box-checking. A lot of it is hypothetical and relies on attackers exploiting a chain of multiple bugs that they probably won’t ever find…. But you still gotta fix it.
There’s no point in being so proud of your code and dismissing security concerns because you’re arrogant enough to think it can’t happen to you. Just learn to fix it and move on with your life.
Maybe someone should fork Opencart and patch the security vulnerabilities and try to drive people away from this guy's repo, since he's just combative anytime someone raises a concern.
Or quit using his code altogether.
Given a rant like this I wouldn't be trusting his code. Admin access to a backend and ability to write to the underlying filesystem+configs are two different layers. Yeah in many cases they may be the same admin, but not necessarily. It also means a compromised admin UI user can modify the underlying system to hide their tracks.
It's like saying it's ok to have a hypervisor breakout because it requires you to have root in the underlying VM to exploit and only trusted admins have root...
Also this issue, ooof https://github.com/opencart/opencart/issues/12939
Wow, his response. Someone needs to fork this project because this guy isn't living in the real world.
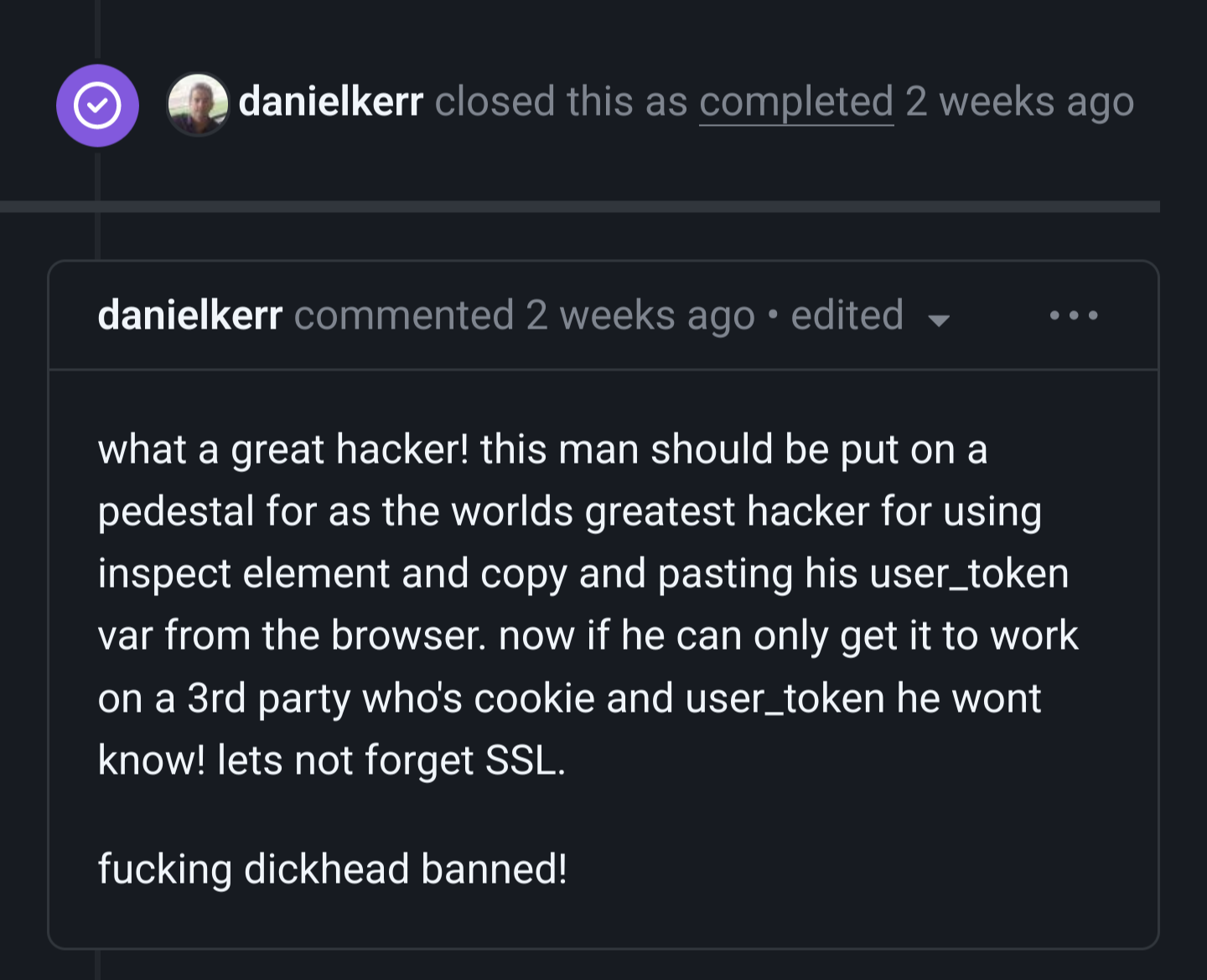
[This comment has been deleted by an automated system]
I've been in this guy's shoes.
I used to code a particular project that was somewhat popular in its own little niche. Some guy trying to make a name for himself must have gone through the docs and done everything it said not to; then reports that in such a case, it's insecure.
The other project members and I basically said "well stop doing everything it says not to". But Jerome makes a web page about it; generates a lot of buzz. We amended our docs to restate that if you do all the dumb things, you'll look dumb. And we linked to his page.
Not proud, but we had bigger fish to fry.
Replace that guy with this guy, who will do that to you over legitimate security concerns.
This is just pointless drama. It's an emotional shitshow with way too much ego from all participants. The reaction from the Dev is actually bad, but the OG CVE is equally bad.
On one hand, I don't expect an app to let me inject code even as an admin. That's just very bad form, and asking for trouble.
On the other hand, arguably, if an attacker has admin access, you're toast. So that's also hardly a CVE.
Now, all the involved people have terrible written expression, poor grammar, and are even omitting entire chunks of sentences.
And then there's the content... Nah, this is just noise. Absolute junk. Sorry, but IMHO this has nothing to do in this community.
It's a prime example of how not to act, regardless.
tf was that shit at the end?
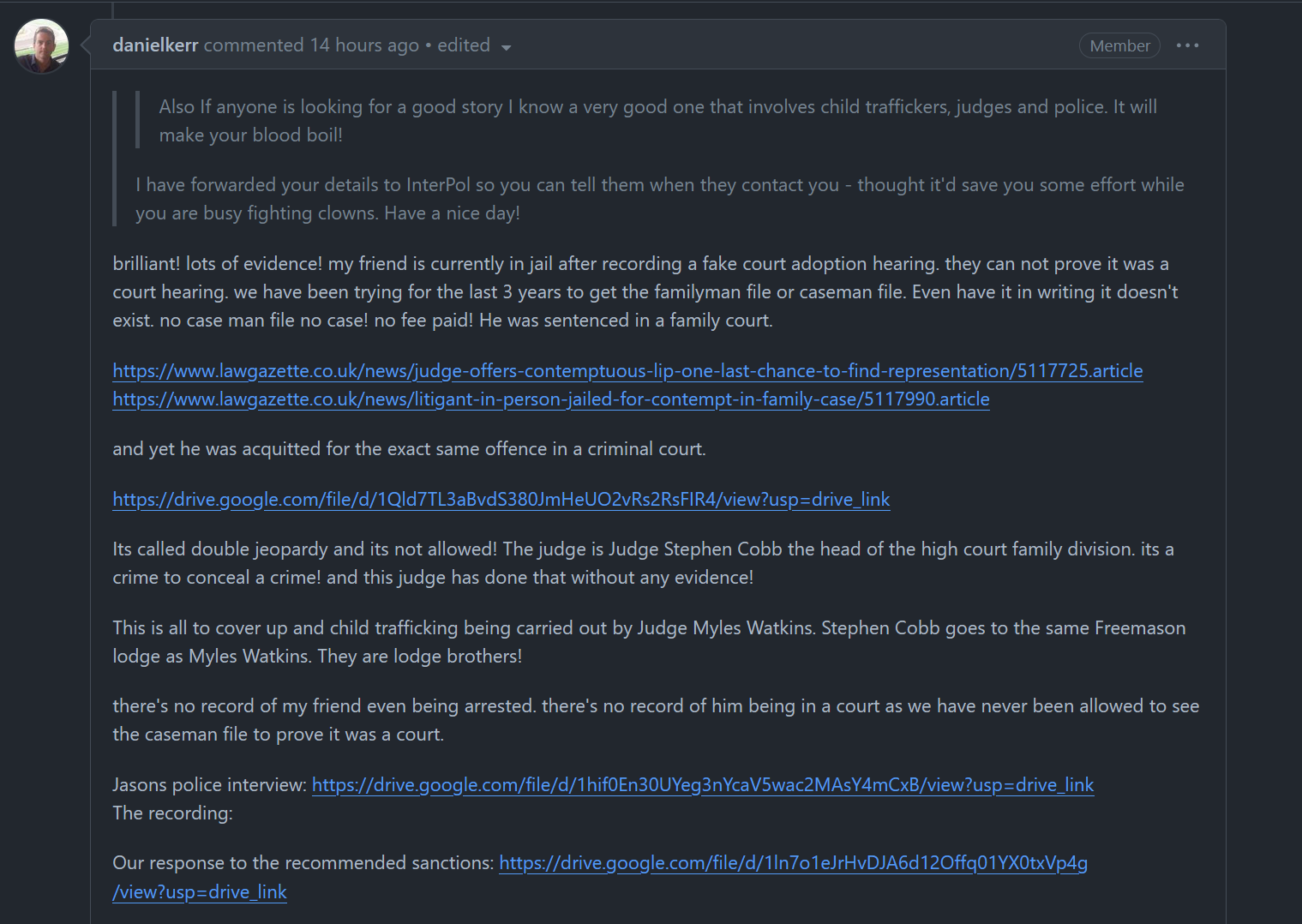
text:
brilliant! lots of evidence! my friend is currently in jail after recording a fake court adoption hearing. they can not prove it was a court hearing. we have been trying for the last 3 years > to get the familyman file or caseman file. Even have it in writing it doesn't exist. no case man file no case! no fee paid! He was sentenced in a family court.
https://www.lawgazette.co.uk/news/judge-offers-contemptuous-lip-one-last-chance-to-find-representation/5117725.article https://www.lawgazette.co.uk/news/litigant-in-person-jailed-for-contempt-in-family-case/5117990.article
and yet he was acquitted for the exact same offence in a criminal court.
https://drive.google.com/file/d/1Qld7TL3aBvdS380JmHeUO2vRs2RsFIR4/view?usp=drive_link
Its called double jeopardy and its not allowed! The judge is Judge Stephen Cobb the head of the high court family division. its a crime to conceal a crime! and this judge has done that without any evidence!
This is all to cover up and child trafficking being carried out by Judge Myles Watkins. Stephen Cobb goes to the same Freemason lodge as Myles Watkins. They are lodge brothers!
there's no record of my friend even being arrested. there's no record of him being in a court as we have never been allowed to see the caseman file to prove it was a court.
Jasons police interview: https://drive.google.com/file/d/1hif0En30UYeg3nYcaV5wac2MAsY4mCxB/view?usp=drive_link The recording:
Our response to the recommended sanctions: https://drive.google.com/file/d/1ln7o1eJrHvDJA6d12Offq01YX0txVp4g/view?usp=drive_link
Legibility wasn't the issue, but I appreciate your transcript anyway.
This is some freeman sounding bullshit
I doubt this guy has a CoC or it's pretty short. The response is even worse than Linus on a bad day.