Disable javascript, trying to get around fingerprinting with javascript enabled is an exercise in futility, and is especially risky with something as heavily monitored as tor.
Privacy
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
Chat rooms
-
[Matrix/Element]Dead
much thanks to @gary_host_laptop for the logo design :)
Disable javascript
This is like those people who say that the only form of safe sex is abstinence. Technically true, practically useless.
I'm slowly starting to agree with @ssm that safeguarding against fingerprinting is an exercise in futility though...QubesOS sounds like something that might help though, since it makes it easy to browse from a virtual machine with fonts and other settings that may be leaked set to the most bog-standard defaults.
On a related note, disabling javascript can actually improve your user experience quite a lot for certain types of tasks. A lot of news/blogs/article-style websites nowadays are actually more usable without javascript, because you don't have to waste time closing all of the ads and cookie popups. I have a separate browser profile with js disabled and use it quite a lot.
No script lets you individually allow js on certain sites, even specific sources. Block all by default, allow safe sites or temporarily allow other sites based on need. I started doing that this year and it hasn't been nearly as much trouble as I thought it would be.
Tor has noscript automatically enabled no?
It should, but I guess this user disabled it. I visited the same site with javascript disabled and it can't fingerprint it (not in tor browser, I don't trust it (css has nasty fingerprinting capabilities, huge mozilla codebase), I use w3m with torsocks and my useragent set to tor browsers, also tested qutebrowser with js disabled).
Which browser do you use?
stated in post, w3m, a text browser (unless it wasn't there when I last edited it, I'm a very sporadic editor)
Never heard of w3m, will check it out
Edit: I thought I was paranoid for using tor as a daily browser lmao
Tor has noscript automatically enabled no?
There's three security settings via NoScript in Tor browser. The default has JS enabled.
It does, but you have to manually configure it to turn off javascript entirely.
Disable javascript, trying to get around fingerprinting with javascript enabled is an exercise in futility, and is especially risky with something as heavily monitored as tor.
I like disabling JS myself for some web browsing but this can make fingerprinting easier because most people do enable JS, and I've read that with JS disabled certain things still can be detected through CSS files.
easy, disable css too (text browsers do this) :)
I feel like on Tor specifically, disabled JS is far more common than on clearnet connections so not as big of an issue.
IIRC, it actually goes deeper than just reporting what fonts are installed. Even if the font names and metrics are masked by the browser, scripts can render them to a canvas and sample the resulting pixels.
This is why I don't install any custom fonts where a web browser can use them, and part of why I keep javascript disabled by default.
Out of curiosity, how much of the internet is unusable with js disabled? As in, how often do you run into sites that are essentially non-functional without?
I haven't taken measurements, but there are many problematic sites these days. Lots of web developers fail to see the problems that javascript imposes on users, so they build web apps even when they're serving static content, where a regular web site (perhaps with javascript enhancements that aren't mandatory) would do just fine.
I selectively enable first-party scripts on a handful of sites that I regularly use and mostly trust (or at least tolerate). Many others can be read without scripts using Firefox Reader View. I generally ignore the rest, and look elsewhere for whatever information I'm after.
Thank you for the information! I kind of suspected it'd be like that tbh,
Don't bother https://noscriptfingerprint.com/
There's also TLS-based fingerprinting which cloudflare uses to great success, no html/css/js even needed for that.
how much of the internet is unusable with js disabled
Quite a lot actually. A lot of articles / blogs / news sites are actually more usable without javascript than with, because none of the annoying popups and shit can load. I suggest having two browser profiles: one with javascript enabled by default, and one with javascript disabled. So for things like online shopping, you'd open the js profile. And for things where you expect to do a lot of reading, use the nojs profile. Ublock origin also lets you temporarily enable/disable js for a particular website pretty easily.
I wonder if running it in a container such as flatpak would help.
Flatpak is not a container and should not be thought of as such for security/privacy purposes:
In general though we try to avoid using the term container when speaking about Flatpak as it tends to cause comparisons with Docker and rkt, comparisons which quickly stop making technical sense due to the very different problem spaces these technologies try to address. And thus we prefer using the term sandboxing.
https://flatpak.org/faq/#Is_Flatpak_a_container_technology_
It can provide container-like functions if specifically configured for that, but that's not normal and it shouldn't be relied on as a security barrier.
I would not count on it, since it's required for proper theme integration. A quick search confirms my suspicion: some font direcories are mapped.
I quite like the idea though, sort of a lite qubes or unmodified VM for all Firefox Flatpak users could be nice.
In a perfect world, it would be nice to have a checkbox per app where I can select whether it should share anything with the system libraries.
Not sure whether it can fix the font problem, but in general Flatseal allows you to customise permissions for installed flatpaks.
I'm running Brave and Librewolf from flatpak. Nope, it doesn't help, at least with default sandbox settings.
Is trust score 0 good or bad? I use uBlock with canvas blocker (fakes canvas) and some settings like referer.xorigin.trimming.
Doesn't work for Tor Browser also: shows different fingerprints after a full relaunch of the browser.
There's something beautiful about the simplicity of Gemini in Kristal and LaGrange.
You set your font and colors offline and it's universal.
Hyper Text Web is great but I wonder if we will see a return to simplicity in high tech circles now that the Net is the new "Television Rules The Nation"
I’m an iOS user who has not installed custom fonts. I’m sure I’m not the only one. Certainly that wouldn’t provide much useful information?
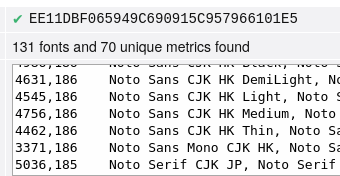
I think it may be fonts embedded in the thing already. Noto is kind of standard because it supports everything.
This is what I though as well, but brave on stock windows doesn't show any noto fonts. Haven't tested tor browser on windows yet tho, so idk
Does every Tor browser show the same fonts? That's whats important.
Okay, I just tested Tor on windows, and it shows a bunch of microsoft fonts that my linux box doesn't have.
But what I did notice is that the fingerprint changed on my linux box after a full restart of tor browser. So I guess their approach is to randomize fingerprints between sessions, rather then to keep everyone's fingerprint the same?
Submit a bug report
There's a summary here with some Tor browser findings : https://gitlab.torproject.org/tpo/applications/tor-browser/-/issues/18097#note_2961761
OK, my fingerprint for Tor Browser is 0b8c195e60af3e2c29ebb8adecb340b1. Is it so unique? What is yours?
I guess the important thing is in the unique versus total in for example 200 fonts and 150 unique metrics found.
It doesn't matter really, one can write any words on a webpage, but show me the proof e.g. an unique and permanent resulting fingerprint.
I see from topics like this that many people don't understand fingerprinting, just showing a fingerprint, a soft of ID means nothing. A fingerprint must be:
- Unique for a particular browser instance, or at least effectively rare. For example, when the same browser on different distros shows different fingerprints.
- Permanent, the same each time you launch the browser.