Malicious Compliance
People conforming to the letter, but not the spirit, of a request. For now, this includes text posts, images, videos and links. Please ensure that the “malicious compliance” aspect is apparent - if you’re making a text post, be sure to explain this part; if it’s an image/video/link, use the “Body” field to elaborate.
======
-
We ENCOURAGE posts about events that happened to you, or someone you know.
-
We ACCEPT (for now) reposts of good malicious compliance stories (from other platforms) which did not happen to you or someone you knew. Please use a [REPOST] tag in such situations.
-
We DO NOT ALLOW fiction, or posts that break site-wide rules.
======
Also check out the following communities:
!fakehistoryporn@lemmy.world !unethicallifeprotips@lemmy.world
view the rest of the comments
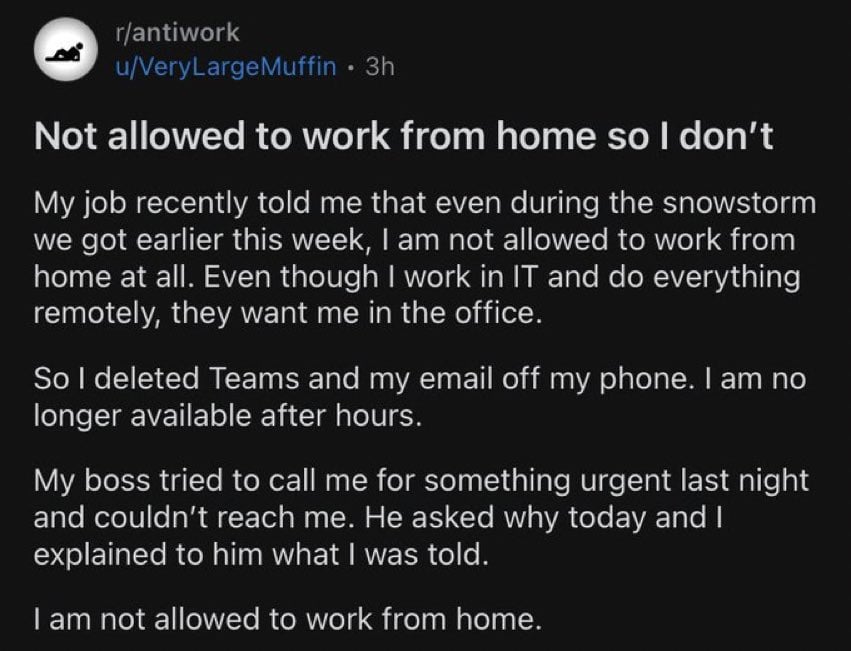
You're talking about MDM in Intune which is only used on corporate owned devices. MAM is used for personal devices and does not have device administration access. It's in the name - Mobile Application Management.
https://learn.microsoft.com/en-us/mem/intune/fundamentals/intune-planning-guide#personal-devices-vs-organization-owned-devices
This implies that the company has a competent IT team that rolls it out correctly, and that there won't be some way to exploit it and dig in further than expected.
Also:
(From the site)
Lmao WHAT? It's normal for users to do company shit on their personal phone? What kind of delusional Spongebob bullshit is that? Is the company gonna pay for data or subsidize the cost of my phone? Are they going to pay me to be on call if they expect me to of this shit outside of my working hours?